Commercial Pain Points: Security as a Secondary Concern
| Published: | Wednesday, October 1, 2025 |
| Author: | Daniel Patterson |
Unmasking the opacity of proprietary vendors and illuminating the open-source path to resilience
Introduction
In the current digital landscape, security is often treated as an afterthought rather than a cornerstone. Nowhere is this more evident than in the practices of proprietary technology vendors, who operate under a veil of secrecy when it comes to vulnerabilities, breaches, and internal security processes. The lack of transparency has repeatedly left individuals, organizations, and entire societies vulnerable to harm, while users are made to shoulder the burden of protection.
This persistent opacity isn't just inconvenient, but is symptomatic of a deeper issue within proprietary ecosystems. Data and privacy concerns are magnified when those entrusted with safeguarding information deliberately obscure their practices. In stark contrast, the open-source community has cultivated a model of security rooted in transparency, accountability, and shared responsibility. This article will explore the flaws of proprietary approaches and contrast them with the resilience made possible through open collaboration.
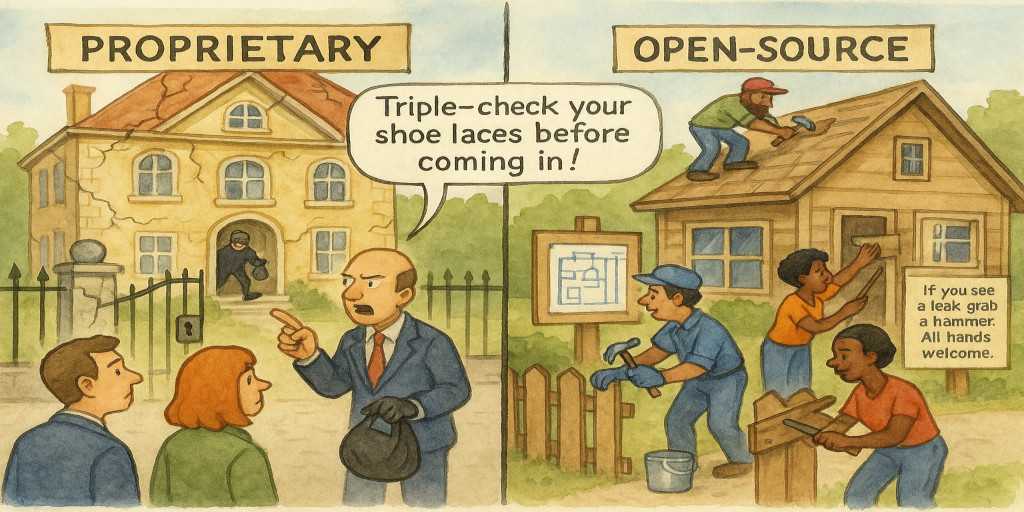
The Proprietary Vendor's Security Theater
In the realm of proprietary technology, security is often presented as a polished performance, complete with scripted assurances, glossy marketing, and a carefully curated illusion of control. Yet behind this facade lies the troubling reality of a long-standing pattern of breaches, obfuscation, and reactive damage control. This section explores how major vendors have repeatedly failed to safeguard user data, deflected responsibility, and resisted meaningful transparency. It reveals how the architecture of these systems is not designed for resilience, but for containment, where the priority is not preventing harm, but managing perception. The result is a landscape where users are burdened with the illusion of agency, while the true vulnerabilities remain permanently hidden behind closed doors.
Legacy of Breaches and Broken Trust
Since the mid-1990s, the world has witnessed a steady cascade of data breaches, each challenging the legitimacy of institutions tasked with protecting private information. These incidents have rarely been minor. Personal records, creative works, financial details, and even intimate communications have been exposed, often falling into the hands of actors motivated by profit or disruption. What began as sporadic intrusions has become a recurring pattern, to the point where breaches are now the norm rather than the exception.
The cumulative effect of these failures is profound. Individuals are left vulnerable to identity theft, fraud, and exploitation. Meanwhile, organizations face reputational damage that lingers long after the breach is disclosed. At the root of this crisis lies a consistent unwillingness to acknowledge systemic flaws and the near total absence of genuine accountability.
Shifting Blame to the Customer
As breaches continue to occur, proprietary vendors have increasingly perfected the art of deflecting responsibility. Instead of confronting their own infrastructural weaknesses, they impose increasingly rigid security protocols on customers. Users are expected to create complex passwords, rotate them frequently, pass multi-layer authentication hurdles, and navigate ever-changing security dashboards.
While these measures could be useful in a certain limited sense, they obscure the fundamental truth that the breach rarely occurs because of user negligence. Most often, it is the vendor's own systems that contain the exploitable flaw, or it is human manipulation, otherwise known as social engineering, that bypasses even the most secure defenses. The burden of coping with the damage of the compromise is shifted unfairly, placing individuals in a defensive posture while the systemic issues remain utterly unaddressed.
Obscured Boundaries and Simulated Assurance
Another hallmark of proprietary vendors is their reliance on simulated assurance. Security claims are expressed in vague language, and represented by inane certifications or badges that lack any independent validation. Customers are left to infer that testing has been thorough, when in reality the exercises often resemble what are referred to as unit tests, which are controlled, predictable, atomic, and far removed from real-world adversarial conditions.
There is little transparency in how these systems are evaluated, and full-force independent third-party audits are rare, if used at all. Even in the cases of the most sought-after certifications, it is completely left to the organization to assert that they meet all of the specified standards, although some superficial, well-categorized tests are performed during the physical audit. The final result, however, is a carefully cultivated appearance of diligence that masks the absence of any meaningful safeguards while they are back on the streets.
Silence Until Exposure
Perhaps the most troubling behavior of proprietary vendors is their habitual silence. Breaches are rarely disclosed proactively, if at all, in some cases. Instead, they come to light through whistleblowers, investigative journalists, or regulatory inquiries. Until that moment of exposure, users remain in the dark, continuing to entrust their data to systems that may already have been compromised a long time ago.
This reactive posture undermines trust at its core. By withholding information, vendors delay the protective measures that individuals and organizations might otherwise take. The damage compounds, and the eventual disclosure often feels less like accountability and more like an admission forced by circumstances. The sheer lack of scandal around this continuing issue seems ever more puzzling.
Superficial Fixes and Recurring Vulnerabilities
When the pressure to respond becomes unavoidable, proprietary vendors typically resort to superficial fixes. A patch is issued, but it addresses only the specific exploit rather than the deeper architectural weakness that made the attack possible. The cycle then repeats. Attackers adapt with minor modifications, and the system is exposed once again, with a larger compromise than had previously been achieved in some cases.
This pattern of denial, minimal intervention, and recurring vulnerability is unsustainable. It demonstrates not only a lack of foresight but also a disregard for the long-term well-being of the public, who require computerized functionality to remain productive and competitive in modern society. Security, under this model, is not a primary foundational concern, but a secondary inconvenience that is managed only when absolutely necessary.
The Open-Source Community's Transparent Alternative
In stark contrast to the proprietary model, the open-source community embraces a philosophy of openness, collaboration, and shared accountability. Here, security is not a performance, but a process, continuously refined through collective insight and public scrutiny. This section highlights how open-source projects foster environments where vulnerabilities are exposed early, addressed transparently, and resolved through community-driven effort. It demonstrates how the absence of secrecy leads to stronger systems, not weaker ones, and how the principle of openness transforms security from a reactive obligation into a proactive commitment. In this model, users aren't just passive recipients of protection, but active participants in its evolution.
A Culture of Shared Responsibility
Open-source technology presents a fundamentally different approach. Here, security isn't something hidden behind closed doors, but is embraced as a collective responsibility. Developers, maintainers, and users all play active roles in identifying, reporting, and addressing vulnerabilities. Instead of concealing flaws, open-source communities acknowledge them openly and treat them as opportunities for collective improvement.
This shared responsibility creates a resilience that no single vendor can replicate. The act of participation itself becomes a form of protection, as thousands of eyes work together to strengthen the system.
Transparency as a Default
Unlike proprietary systems, where complete secrecy at all times is the common goal, open-source projects operate under a principle of radical transparency. The source code is openly available, allowing anyone to inspect it, test it, or suggest improvements. This openness discourages malicious behavior while accelerating the discovery of weaknesses.
Transparency doesn't mean perfection, but it ensures honesty. Vulnerabilities aren't hidden from users, but are part of an ongoing dialogue between creators and participants. This dialogue, grounded in openness, fosters trust rather than eroding it.
Real-World Testing and Community Validation
The strength of open-source security lies in its constant exposure to real-world conditions. Instead of relying on simulations, open-source software is tested daily by a diverse global community. Each deployment in a different context serves as a form of stress testing, uncovering weaknesses that no laboratory environment could have anticipated.
This breadth of scrutiny far surpasses the limited scope of proprietary testing. Community validation provides a realistic measure of security readiness, informed by lived experience rather than staged environments.
Immediate Disclosure and Collaborative Remediation
When vulnerabilities are discovered, open-source communities typically respond with immediate disclosure. The goal is not to protect the reputation of the project but to protect the users who depend on it. Fixes are developed collaboratively, often within days or even hours, and the process is documented for all to see.
This practice builds trust. Users know that they are not being kept in the dark, and they can witness the problem-solving process as it unfolds. Swift, transparent action ensures that security is treated as more of a priority than an afterthought.
Evolving Defenses Through Collective Insight
Finally, open-source projects benefit from a dynamic process of evolution. Each incident adds to the collective wisdom of the community, shaping future defenses. The vigilance of the community extends far beyond preventing attacks. It includes identifying invasive practices, tracing the misuse of data, and advocating for fair treatment of creators.
In this way, open-source security does more than guard against harm. It also raises public expectations, and demands that systems respect their users, acknowledge their contributions, and reward the labor that sustains them.
Conclusion
The contrast could not be clearer. Proprietary systems, built on secrecy and reactive fixes, perpetuate a cycle of insecurity and eroded trust, while open-source systems, grounded in transparency and shared responsibility, offer a model of resilience that empowers individuals and communities alike.
Security can't remain a secondary concern, treated only when breaches force it into the spotlight. It must be embedded into the very fabric of the systems we rely on. By choosing open technologies, individuals not only reclaim autonomy over their data but also participate in a culture that values honesty, accountability, and security as a foundational principle.
 werMake
werMake